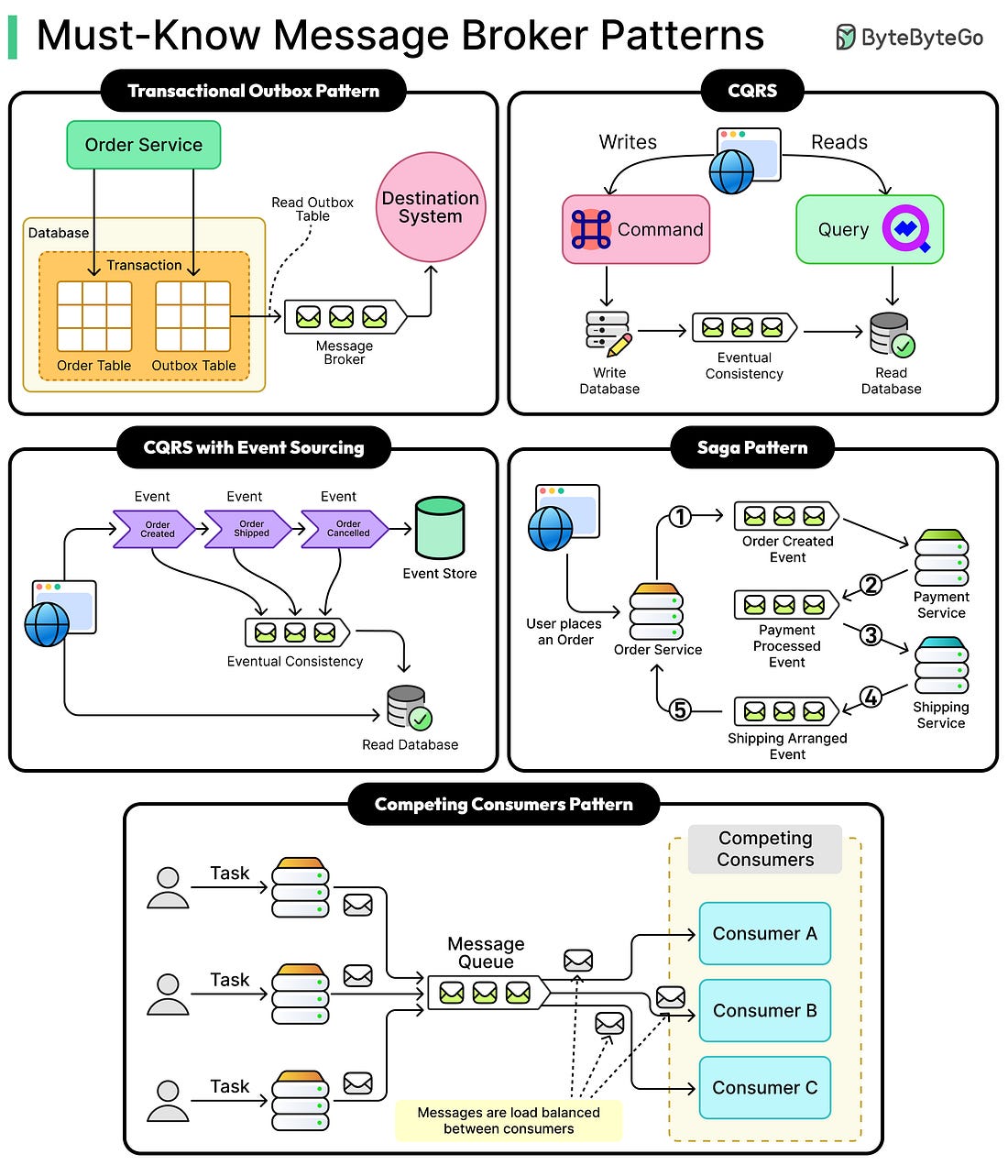
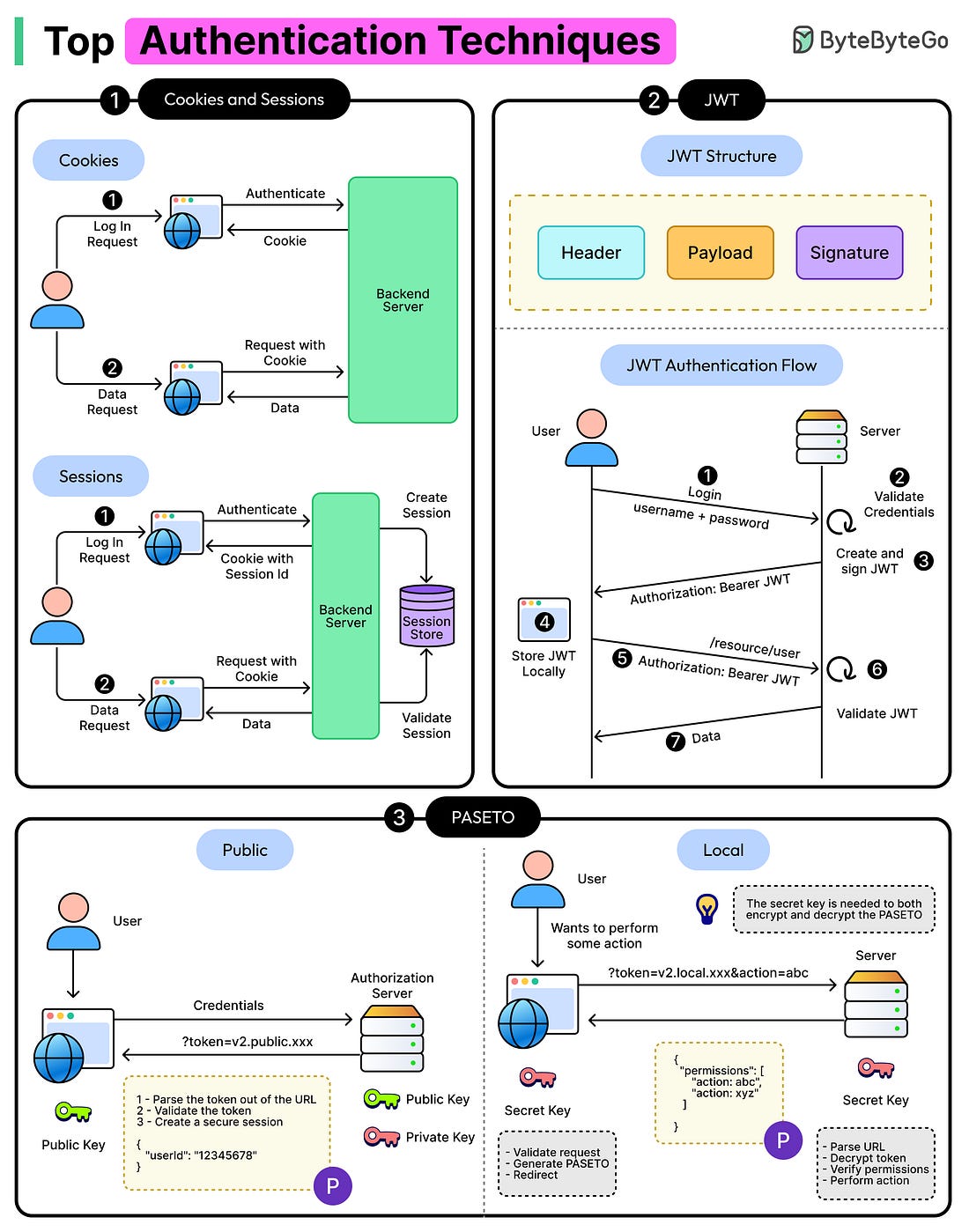
|
Latest articles
If you’re not a subscriber, here’s what you missed this month.
To receive all the full articles and support ByteByteGo, consider subscribing:
Authentication serves as the first line of defense in ensuring the security of applications and the sensitive data they handle. Whether it’s a personal banking app, a corporate platform, or an e-commerce website, effective authentication mechanisms are needed to verify the identity of users and safeguard their access to resources.
Without proper authentication, applications are vulnerable to unauthorized access, data breaches, and malicious attacks, potentially resulting in significant financial loss, reputational damage, and privacy violations.
In addition to security, authentication plays a critical role in the user experience. By identifying users, applications can provide personalized services, remember user preferences, and enable functionalities like Single Sign-On (SSO) across platforms.
With evolving threats, implementing secure and efficient authentication is more challenging than ever. Developers must navigate between competing priorities such as security (ensuring protection against different attack types like session hijacking, token theft, and replay attacks), scalability (supporting millions of users without compromising performance), and user experience (maintaining ease of use while applying strong security measures).
To tackle these challenges, developers rely on various authentication techniques. In this article, we’ll explore multiple authentication techniques used in applications and understand their advantages and disadvantages.